LDAPS¶
LDAP over SSL, or LDAPS, allows you to encrypt your LDAP server data while it travels during communications, in order to protect it from attacks like certificate theft. For more information, see the official Keycloak documentation on LDAPS.
On this page:
Prerequisites¶
You must have the Java jre package installed to complete this procedure.
Establishing LDAPS¶
Open a terminal and connect to your instance of Anaconda Server.
Generate a truststore on your host by running the following command:
# Replace <PASSWORD> with the password for your truststore file # Replace <CA_CERT> with the path to the root certificate authority keytool -keystore truststore.jks -storepass <PASSWORD> -noprompt -trustcacerts -importcert -alias ldap-ca -file <CA_CERT>
Copy the
truststore.jksfile you just generated to the following location:/opt/anaconda/repo/config/keycloak
Find and open your
docker-compose.ymlfile in your installer directory using your preferred file editor.Find the
services: keycloak: volumes:section of the file and add the following line:- ${BASE_INSTALL_DIR}/config/keycloak/truststore.jks:/opt/keycloak/keystores/truststore.jksFind the
services: keycloak: depends_on:section of the file and add the following line:# Replace <PASSWORD> with the password for your truststore file command: /opt/keycloak/entrypoint.sh --import-realm --spi-truststore-file-file=/opt/keycloak/keystores/truststore.jks --spi-truststore-file-password=<PASSWORD>
Caution
Pay close attention to the indentation of your added lines. If you do not add them at the correct level of indentation, your configurations will not be readable.
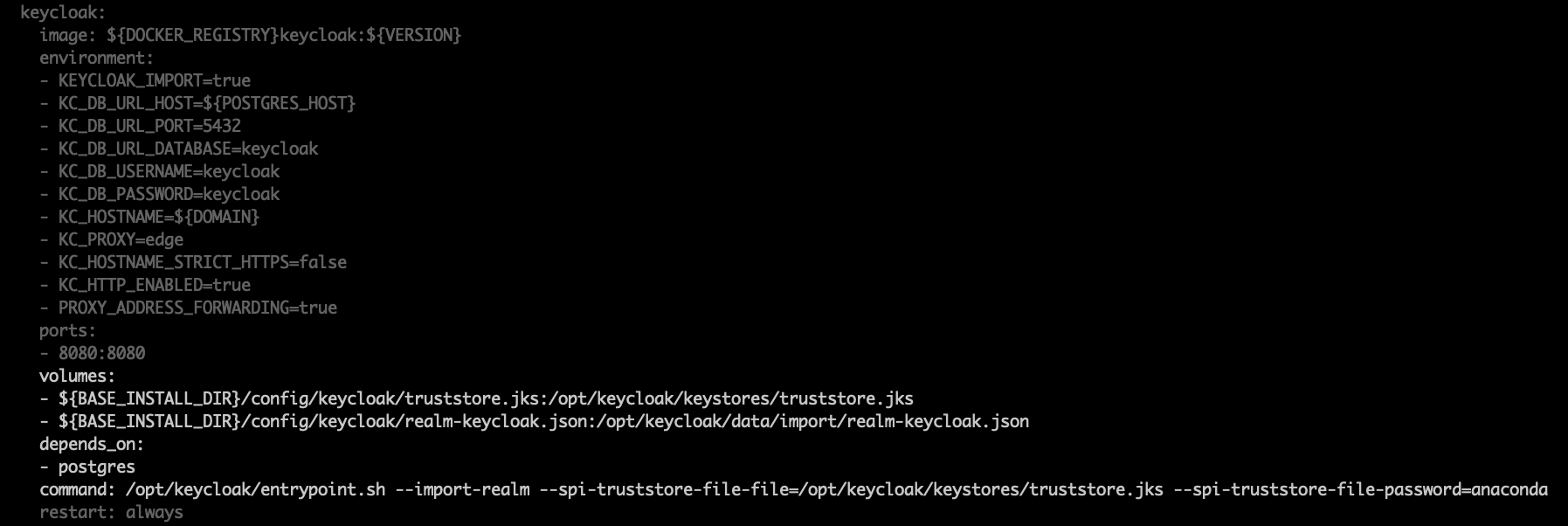
Here is an example of what your
docker-compose.ymlfile should look like when you are finished adding these lines:Enter your base installer directory by running the following command:
# Replace <INSTALLER_DIR> with your installer directory folder cd <INSTALLER_DIR>
Restart your containers by running the following command:
docker-compose up -d
Troubleshooting¶
If you have any issues, verify the certificate authority against the LDAPS server by running the following command:
# Replace <CERT_AUTH.pem> with your certificate authority
openssl s_client -CAfile <CERT_AUTH.pem> -connect ldapserver.com:636
This returns the following string:
Verify return code: 0 (ok)
You can inspect the keystore you created with the following command:
# Replace <PASSWORD> with the password for your truststore file
keytool -list -v -keystore /opt/keycloak/standalone/configuration/keystores/truststore -storepass <PASSWORD>