Roles and permissions#
Roles#
Roles determine the level of access a user has within Package Security Manager. Some preconfigured roles have been embedded into Keycloak to provide users with varying levels of access to the software’s available features. If the default Anaconda roles described here do not suit your use case, you can create a custom role for your users.
Permission levels#
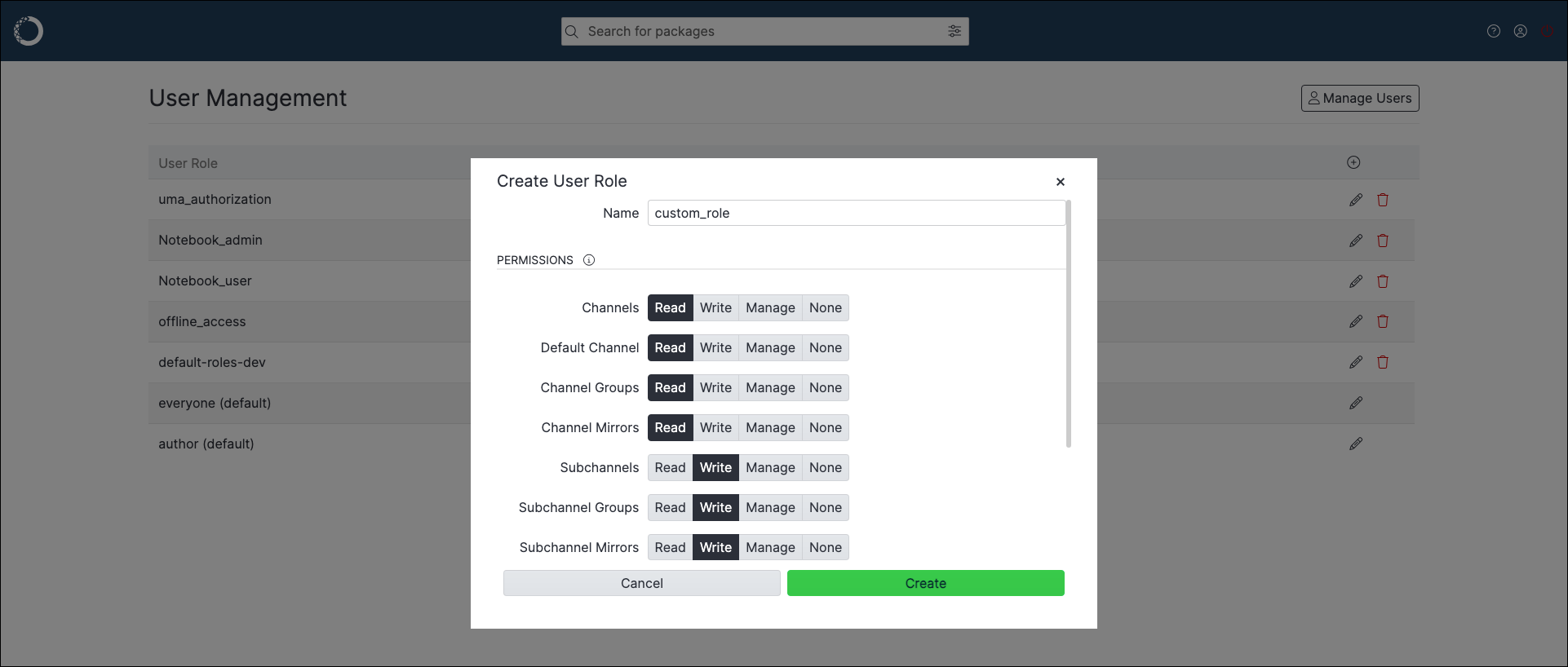
There are four levels of permissions available for Package Security Manager:
Read - provides the ability to view the associated feature.
Write - provides the ability to view and create new assets of the associated feature.
Manage - provides the ability to view, create, and edit assets of the associated feature.
None - removes permissions for the associated feature.
Permission categories#
Each permission category is associated with some feature of Package Security Manager. The available permission categories are:
Channels - grants interaction with channels
Default Channel - grants interaction with the user’s default channel
Channel Groups - grants interaction with channel groups
Channel Mirrors - grants interaction with channel mirrors
Subchannels - grants interaction with subchannels
Subchannel Groups - grants interaction with subchannel groups
Subchannel Mirrors - grants interaction with subchannel mirrors
Artifacts - grants interaction with artifacts
CVE - grants interaction with CVEs
Roles - grants interaction with roles
CVE Notifications - grants interaction with channel CVE notifications
Audit Logs - (read permissions only) grants admins permissions to download user audit logs report
Policy Engine - grants interaction with the policy engine
Preconfigured roles#
Package Security Manager contains the following preconfigured roles for the Dev realm:
everyone - A non-authenticated user. Allows visibility into public channel and subchannel contents as well as group membership.
author - An authenticated user. Allows users to create new channels and subchannels, and provides user level access to your Team Notebooks server.
admin - The administrator role has full management permissions over all the features of Package Security Manager. The admin role is responsible for creating and maintaining mirrors in addition to managing users and CVE data. This role also provides admin level permissions to your Team Notebooks server.
Notebooks admin - An administrator role for the Team Notebooks server.
Notebooks author - Allows users to access the Team Notebooks server.
Note
The admin role is not visible through Package Security Manager UI.
Managing Roles#
For Business-tier customers, Anaconda has two main user personas: IT administrators and everyone else. As an IT administrator, you are responsible for establishing and maintaining the users’ accounts and the resources available to them within Package Security Manager.
Creating custom roles#
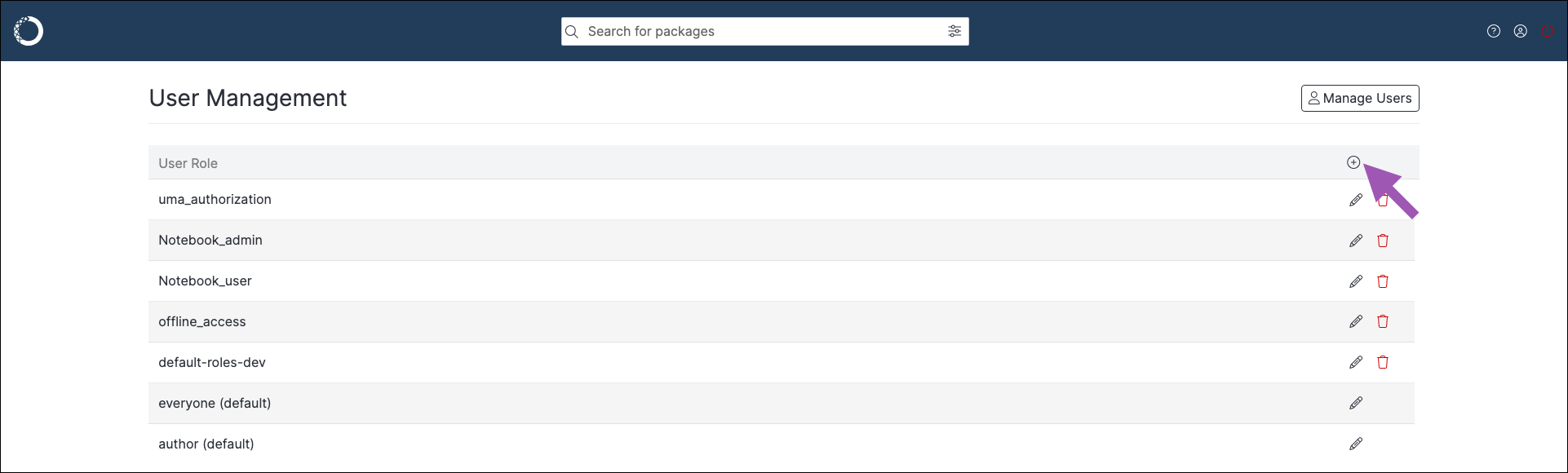
To create a custom role:
Editing role permissions#
To edit your role permissions:
Log in to Package Security Manager.
Select Manage Users from the left-hand navigation.
Select an existing role from the list.
Click Edit role beside the role you want to modify.
Click Update.
Assigning a role to a user#
To assign a role to a user:
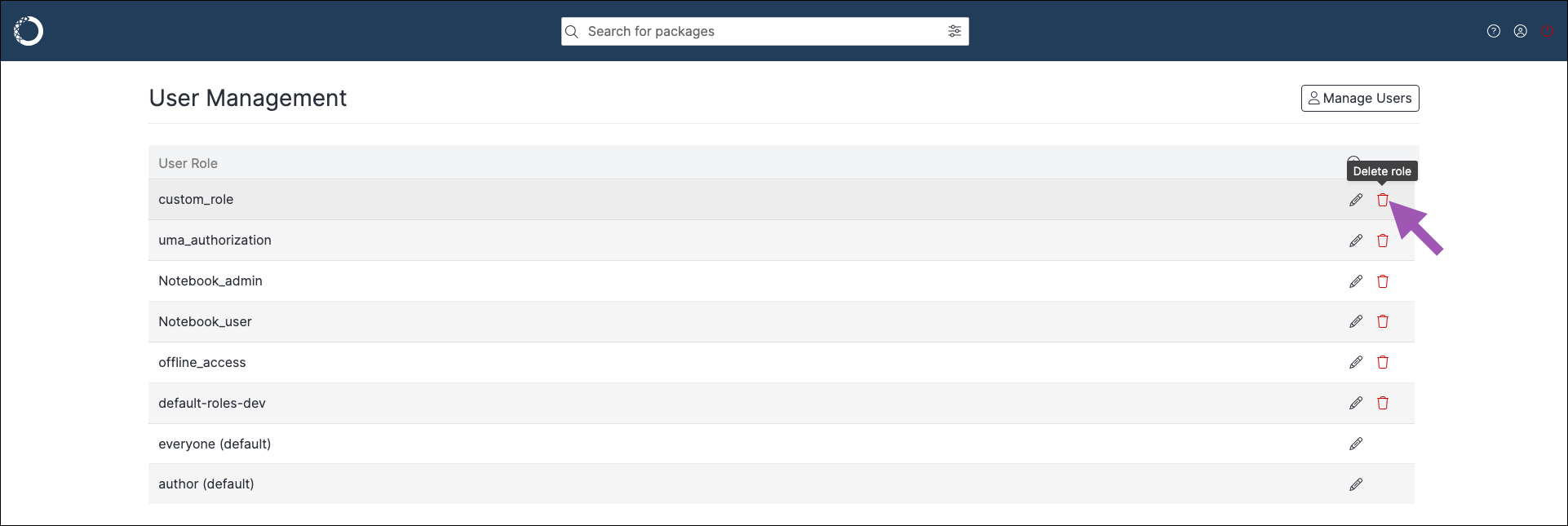
Deleting a role#
To delete a role:
Composite roles#
A composite role is built from other existing roles and provides the aggregated permissions of all the roles it’s composed of.
In the following example, we create a composite role that allows an admin user on the master realm to manage users on the dev realm. However, you can use this same process to create admin roles with restricted access to managing other things on the dev realm.
To create an admin role with restricted permissions:
Navigate to the master realm.
Select Realm roles from the left-hand navigation.
Click Create Role.
Enter a name for your role and provide a brief description of its intended use.
Click Save. More tabs appear.
Open the Action dropdown menu and select Add associated roles.

If necessary, open the filter dropdown menu and select Filter by clients.
To achieve the desired result of creating an admin user that can only view and manage users on the dev realm, select the following available client roles:
manage-users
query-users
view-users
Select available roles to associate their permissions with this composite role.
Click Assign.
Setting/updating default roles#
Default roles are permissions that are automatically applied to any newly created or imported user. Each realm has its own set of default roles that are applied to users created/imported on that realm. These are composite roles, and must be constructed of other existing roles.
To set the default roles:
Verify you are on the realm you need to set default roles for.
Select Realm settings from the left-hand navigation.
Select the User registration tab.
Click Assign role.

If necessary, open the filter dropdown menu and select Filter by clients.
Select available roles to assign to newly created or imported users.
Click Assign.
Group roles#
Any permissions that can be granted to an individual by assigning them a role can also be granted to multiple people by assigning the role to a group. This is exceptionally useful for Package Security Manager implementations that utilize an LDAP or Active Directory server.
To assign roles to a group:
Verify you are working in the dev realm.
Select Groups from the left-hand navigation.
Select the group you want to provide permissions to.
Select the Role mapping tab.
Click Assign role.
If necessary, open the filter dropdown menu and select Filter by clients.
Select available roles to assign to newly created or imported users.
Click Assign.
Setting/updating default groups#
Setting default groups will automatically assign group membership to all newly created or imported users.
To set the default groups: