Tokens#
Authorization tokens can be generated by users and admins to provide others with access to private/authenticated channels or with a specific set of permissions when using the Package Security Manager CLI or API.
This token can be used in place of username-based authentication, and is particularly useful (and sometimes necessary) for third-party applications or automation tools.
Token Types#
There are two types of tokens within Package Security Manager:
Resource tokens#
Resource tokens provide the token holder with read, write, or manage permissions for a specific set of channels.
Scope tokens#
Scope tokens provide the token holder with a fine-grained set of custom user permissions, limiting the available actions that they are able to perform. A scope combines permission categories with specific actions users can perform into a concatenated string, like this:
category:action or category.subcategory:action
Note
Tokens cannot contain both resources and scopes.
Some actions are also tied to permission levels. For example, if you provide the scope channel:edit, you are also providing manage level permissions over channels.
Available scopes
Permission Categories
Available Scopes (category:action)
Associated permissions
Artifacts
artifact:create
Write permissions to parent resource (channel or subchannel)
artifact:delete
Manage permissions to parent resource (channel or subchannel)
artifact:download
Read
artifact:edit
Manage permissions to parent resource (channel or subchannel)
artifact:view
Read
Channels
channel:create
Write
channel:delete
Manage
channel:edit
Manage
channel:history
Manage
channel:view
Read
channel:view-artifacts
Read
Default Channel
channel.default-channel:edit
Manage
Channel groups
channel.group:edit
Manage
channel.group:view
Read
Channel mirrors
channel.mirror:edit
Manage
channel.mirror:view
Manage
Subchannels
subchannel:create
Manage permissions to parent channel
subchannel:delete
Manage
subchannel:edit
Manage
subchannel:history
Manage
subchannel:view
Read
subchannel:view-artifacts
Read
Subchannel groups
subchannel.group:edit
Manage
subchannel.group:view
Read
Subchannel mirrors
subchannel.mirror:edit
Manage permissions to parent channel
subchannel.mirror:view
Manage
Mirrors
mirror:view
Manage
Licenses
system.license:edit
Manage
system.license:view
Manage
CVEs
cve:edit
Manage
cve:view
Read
Roles
role:edit
Manage
role:view
Read
System blobs
system.settings:edit
Manage
system:delete-blobs
Manage
Tokens
user.token:edit
Manage
user.token:view
Manage
Generating tokens#
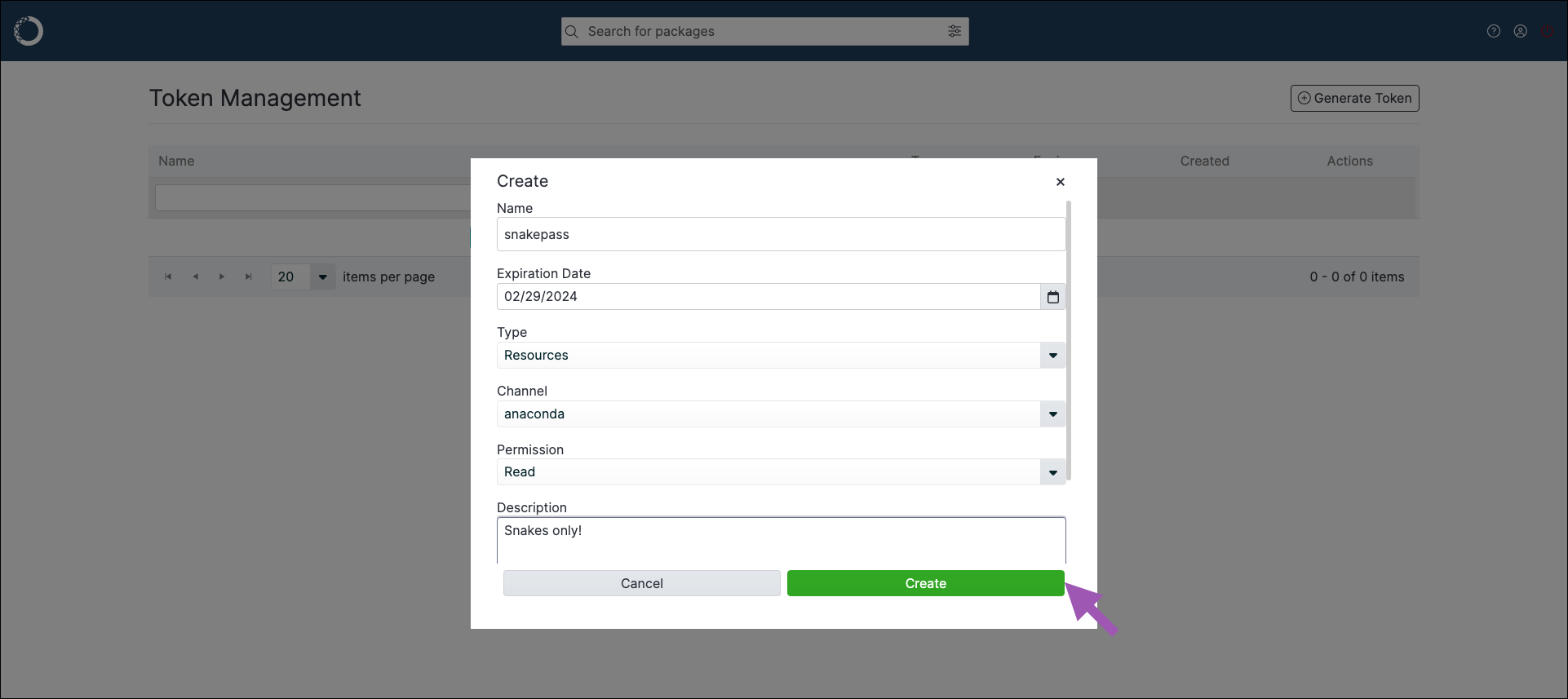
To provide token holders with access to a channel:
Log in to Package Security Manager.
Select Tokens from the left-hand navigation.
Click Generate Token.
Enter a name for your token.
Set an expiration date for your token.
Open the Type dropdown menu and select Resources.
Open the Channel dropdown menu and select an available channel to associate with this token.
Select the level of permissions to associate with this token.
If necessary, click the Add Resource button to include an additional channel with this token, repeat as needed.
Provide a brief description of the token’s use.
Click Create.
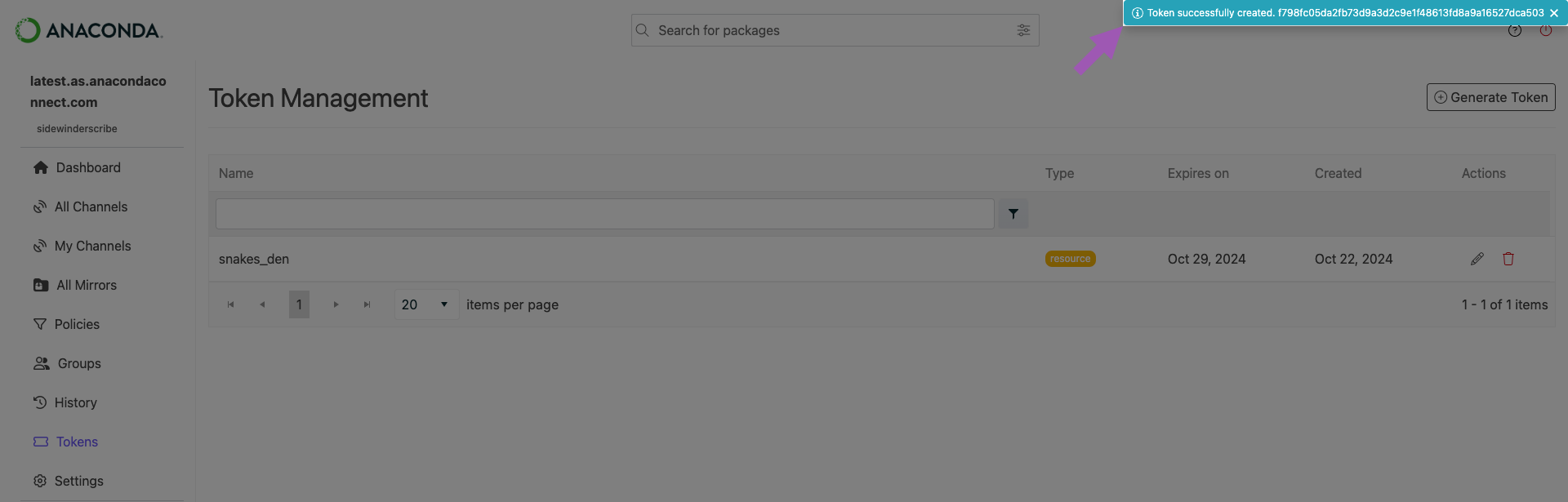
Save your token string in a secure location.
Caution
Generated tokens appear in the upper right corner, and will remain visible until you close the notification, or navigate away from the page.
Save your token in a secure location! If you lose your token, there is no way to recover the token string. You must issue a new token if you lose your current token.
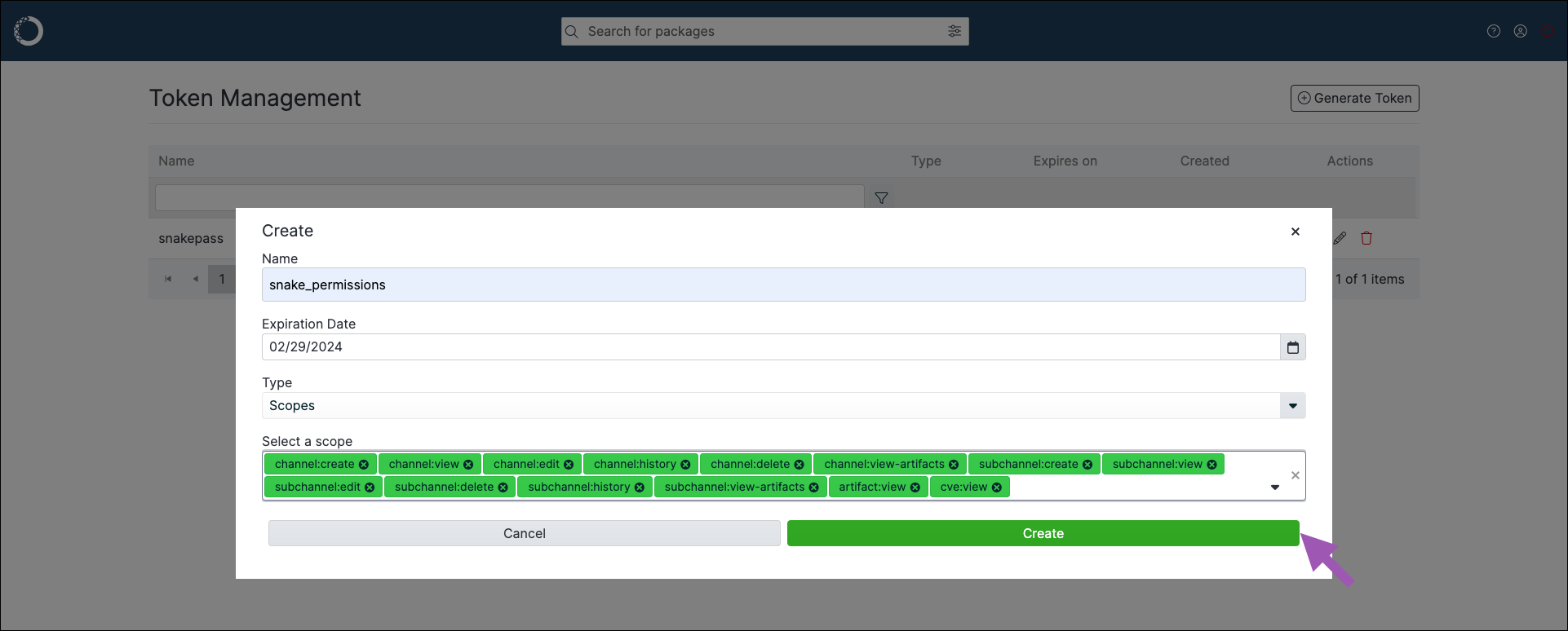
To provide token holders with a custom set of permissions:
Log in to Package Security Manager.
Select Tokens from the left-hand navigation.
Click Generate Token.
Enter a name for your token.
Set an expiration date for your token.
Open the Type dropdown menu and select Scopes.
Open the Select a scope dropdown menu and select a scope to add to the token. Repeat as necessary to build a custom set of permissions for your token holders.
Click Create.
Save your token string in a secure location.
Caution
Generated tokens appear at the bottom of the page and will remain visible until you close the notification or navigate away from the page.
Save your token in a secure location! If you lose your token, there is no way to recover the token string. You must issue a new token if you lose your current token.

Editing a token#
You can edit a token to change its name or to update its expiration date. You can choose to issue a new token while editing as well, which will invalidate the previous string associated with the token.
To edit a token:
Log in to Package Security Manager.
Select Tokens from the left-hand navigation.
Select the token’s Edit icon.
Make any necessary changes to the token.
If necessary, select the Issue a new token checkbox. A warning appears at the top of the window to inform you that you will receive a new token.
Click Edit.
Deleting a token#
To delete a token:
Log in to Package Security Manager.
Select Tokens from the left-hand navigation.
Select Delete Token beside the token you want to delete.
Click Delete.
Setting/using a token#
Once you have generated a token, you can share it with other users by any method you wish.
If you have received a resource token string from another user and you would like to use it to access packages on a channel, add the channel to your .condarc file by running the following command:
# Replace <FQDN> with the URL of your Package Security Manager fully qualified domain name
# Replace <TOKEN> with the generated/shared token string
# Replace <CHANNEL> with the channel name
conda config --add channels http(s)://<FQDN>/api/repo/t/<TOKEN>/<CHANNEL>
Managing tokens via the CLI#
For more information on working with tokens using the CLI, see Package Security Manager CLI.